Cryptocurrency Wallets - Public and Private Keys (Asymmetric Encryption Animated)
In this video, we explain how pubic and private keys work in cryptocurrency wallets. In short, these wallets use asymmetric ...
Whiteboard Crypto
Lec-83: Asymmetric key Cryptography with example | Network Security
Asymmetric cryptography, is a cryptographic system that uses pairs of keys. Each pair consists of a public key (which may be ...
Gate Smashers
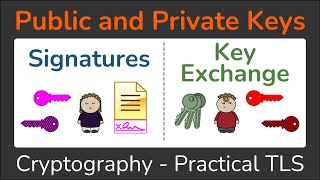
Public and Private Keys - Signatures & Key Exchanges - Cryptography - Practical TLS
Asymmetric Encryption requires two keys: a Public key and a Private key. These keys can be used to perform Encryption and ...
Practical Networking
#27 Principles Of Asymmetric Key Cryptography |CNS|
Telegram group : https://t.me/joinchat/G7ZZ_SsFfcNiMTA9 contact me on Gmail at shraavyareddy810@gmail.com contact me on ...
Trouble- Free
Symmetric Key and Public Key Encryption
Modern day encryption is performed in two different ways. Check out http://YouTube.com/ITFreeTraining or http://itfreetraining.com ...
itfreetraining
PRINCIPLE OF PUBLIC KEY CRYPTOSYSTEM
ROHIT KUMAR
Asymmetric Key Cryptography ll Information and Cyber Security Course Explained in Hindi
Myself Shridhar Mankar a Engineer l YouTuber l Educational Blogger l Educator l Podcaster. My Aim- To Make Engineering ...
5 Minutes Engineering
Public key Cryptography full explain in hindi-Asymmetric key Cryptography,Computer Network Security
Is video mai public key cryptography ya keh sakte hai asymmetric key cryptoy ko bahut ache tarah se explain kia gaya hai...jo ...
Unbeaten Learning
Encryption and public keys | Internet 101 | Computer Science | Khan Academy
Mia Epner, who works on security for a US national intelligence agency, explains how cryptography allows for the secure transfer ...
Khan Academy
1- Public Key Cryptography Arabic Chapter 9
كورس امن المعلومات شرح طريقة التشفير بالمفتاح العام او المفتاح غير المتناظر مع اعطاء مثال عملى لتوضيح الفكرة لاتنسى الاشتراك ...
Code Portal
Public key cryptography: What is it? | Computer Science | Khan Academy
Why do we need public key cryptography? Watch the next lesson: ...
Khan Academy Labs
Public key cryptography - Diffie-Hellman Key Exchange (full version)
The history behind public key cryptography & the Diffie-Hellman key exchange algorithm. We also have a video on RSA here: ...
Art of the Problem
INS: Unit:4 Public key cryptosystem (Asymmetric key Cryptosystem)
Public Key Cryptosystem Asymmetric key Encryption with Public Key Asymmetric key Encryption with Private Key Authentication ...
Twinkal Patel
How asymmetric (public key) encryption works
Easy explanation of "public key encryption". Instead of the usual terms of "public key" and "private key" this tutorial uses "lock" and ...
Veet Vivarto
#28. RSA Algorithm - Asymmetric key cryptography |CNS|
Telegram group : https://t.me/joinchat/G7ZZ_SsFfcNiMTA9 contact me on Gmail at shraavyareddy810@gmail.com contact me on ...
Trouble- Free
Tech Talk: What is Public Key Infrastructure (PKI)?
Learn more about encryption → https://ibm.biz/learn-encryption Check out IBM's data encryption solutions ...
IBM Technology
[HINDI] What is Public Key Cryptography (PKC)? | Types of Asymmetric Encryption | Working Explained
Hello everyone. This is a very important video in terms of Information security and cryptography, where I will brief you about public ...
Bitten Tech
How Public and Private Key Work In Your Crypto Wallets
If you own cryptocurrency, you most likely have a wallet where you keep your coins. However, these cryptocurrency wallets do not ...
CoinGecko
RSA Private & Public Key Encryption in Python
Today we learn how to do asymmetric encryption using RSA and private and public keys in Python.
NeuralNine
Public Key Cryptography
Asymmetric Public Key Cryptography is used for Authentication (Digital Signatures) or Encryption (Public Key Encryption). Link to ...
Biz Sci Tech
Lecture 2: Public-key Cryptography
Public-key cryptography - How does it work? - Public and private keys - One-way functions.
Web3 Foundation
Public Key Cryptography: Diffie-Hellman Key Exchange (short version)
This is a segment of this full video: https://www.youtube.com/watch?v=YEBfamv-_do Diffie-Hellman key exchange was one of the ...
Art of the Problem
The RSA Encryption Algorithm (1 of 2: Computing an Example)
Eddie Woo
public key and private key in Cryptography | in hindi by geeta chaudhary
important.
Short Tricks Learning
Introduction to Public Key Cryptography
Course Grinder
Introduction to Basic Cryptography: Public Key Cryptography
Ryan Riley
Prime Numbers & Public Key Cryptography
A simple explanation of how prime numbers are used in Public Key Cryptography from ABC1 science program Catalyst.
Simon Pampena
Public Key Cryptography التشفير باستخدام المفتاح العام
في هذا الفيديو اعطي فكرة عن طريق استخدام المفتاح العام في التشفير وكمقدمة الى شرح خوارزميات المفتاح العام كخوارزمية RSA.
الدكتور احمد العتوم - أمن سيبراني
Public Key Encryption (PKE) in hindi | Public key encryption example | Digital Forensic
Public Key Encryption (PKE) in hindi | Public key encryption example | Digital Forensic: here i have explained about Public Key ...
Zixplain
Introduction to Public-Key Cryptography
Kiran Kuppa
Public Key Cryptography: Secrecy in Public - Professor Raymond Flood
For centuries massive intellectual effort has gone into methods of ensuring secure communication, because of its importance in ...
Gresham College
What is Encryption? Public Key Encryption? Explained in Detail
Namaskaar Dosto, is video mein maine aapko encryption ke baare mein bataya hai, aap sabhi ne computer aur internet use karte ...
Technical Guruji
Explore Public Key Cryptography!
Get ready to join the blockchain revolution with public, permissionless blockchain No permission slips are needed! Let's rock the ...
Blockchain Seekho
What are Public Keys & Private Keys in #Crypto #cryptowallet
Understand the difference between Public Key & Private Key in crypto.
Sahicoin
Ch9 part1 Public Key Cryptography and RSA
Ahmad AbdAllah Hassan
Exchanging Public Key Certificates
This video is part of the Udacity course "Intro to Information Security". Watch the full course at ...
Udacity
Lec-81: Symmetric Key Cryptography in Network Security with examples
Symmetric key cryptography is any cryptographic algorithm that is based on a shared key that is used to encrypt or decrypt ...
Gate Smashers
IT Security Tutorial - What is public key encryption?
Learn the fundamental concepts for protecting data using public and private key encryption. Explore more IT Security courses and ...
LinkedIn Learning
RSA Algorithm in Cryptography and Network Security
RSA Algorithm In Cryptography and Network Security #RSA #RSAalgorithm #NetworkSecurity #Cryptography Courses on my ...
Abhishek Sharma
Private Key Encryption (Symmetric Key Encryption)
In private key encryption, data is encrypted using a single same key that only the sender and the receiver know. That is why ...
Sunny Classroom
Asymmetric Key Cryptography | RSA Encryption Algorithm | Asymmetric Encryption | Simplilearn
Advanced Executive Program In Cybersecurity (India Only): ...
Simplilearn
Public Key CryptoSystems- Introduction--Principles-KTUCST433 Security in Computing-S7CS-Mod 3-Part 1
Join this channel to get access to perks: https://www.youtube.com/channel/UCNhpTl8Bdn-IDAAI46yqsMA/join.
KTU Computer Science Tutorials