Cybersecurity Roadmap: Global Healthcare Security Architecture
Nick H. Yoo, Chief Security Architect, Global Healthcare IT Using NIST cybersecurity framework, one of the largest healthcare IT firms in the US developed global ...
RSA Conference
Cyber security: Five ways to manage threats and mitigate risk
If a network, identity, device or data is valuable – particularly if it is information tied to intellectual property, financials, sensitive files, critical infrastructure or ...
Meet the Boss
Cyber Threat Information Sharing for Better Cybersecurity
Lessons from The Cyber Past & Information Sharing for Better Security” with Kunal Sehgal (former MD, OT-ISAC) and Bill Nelson (Chair/CEO, GRF and former ...
Benjamin Ang
UCSB iCTF International Capture the Flag Hacking Competition
Professor Giovanni Vigna of UC Santa Barbara introduces the UCSB International Capture the Flag competition (iCTF) held annually and managed by computer ...
UCSB College of Engineering
Critical Partnerships for Cybersecurity
A discussion on public-private cooperation on ensuring cybersecurity of critical infrastructures. For further information, please visit: ...
AtlanticCouncil
Cybersecurity and Healthcare – Trends, Challenges, and Evolving Threats
Part 2 session objectives include: 1) Discussing the trends in cybersecurity, 2) Explaining the business challenges in a cyber world, 3) Discussing the risks ...
JCCCvideo
Inside Public-Private Partnerships
In the past, when governments wanted hospitals or subway lines or train stations built, they hired a company to create that infrastructure, then oversaw the ...
The Agenda with Steve Paikin
The Future of Supply Chain Security | RSAC 2020
As organizations rapidly change supply chain tactics to meet the demands of evolving global ecosystems, security and risk mitigation need to be top of mind ...
RSA Conference
Health Care Cyber Security: How to Mitigate Threats and Manage Risk Through Human Factors
Have you given your health care organization a data-hygiene check-up? Many of today's breaches happen when organizations either lack, or fail to follow, ...
USD Continuing Education
Gus Coldebella: Cyber Security And Geopolitics
The threat of cyber conflict in the 21st Century comes to the forefront with Gus Coldebella. Threats such as industrial sabotage, election meddling, and others ...
GBH Forum Network
Black Sky Resilience: Assessing the Vulnerability of the Electric Grid ... [more]
CREDC Seminar Series. Presented on December 2, 2016 by Jonathon Monken, PJM Interconnection. Full title is "CREDC Seminar Series. Presented on [full ...
CREDC
Edward Snowden: The Man Who Conned the World
About the Lecture: Edward Snowden is a polarizing figure in the world today, known by millions and the press as a champion of freedom and a whistle blower ...
The Institute of World Politics
Debates of the Century @NYU Wagner: National Security (Featuring Edward Snowden and Fareed Zakaria)
Fareed Zakaria and Edward Snowden debate the question: “Government should have lawful access to any encrypted message or device.” Moderated by Barton ...
The Century Foundation
[EXCLUSIVE] Frauds in Korea Election (Walter Mebane)
가로세로연구소 구독 후원 방법 Paypal (해외거주자용) : https://paypal.me/hoverlab USA Citi Bank : Account Number (9250716923), Routing Number ...
가로세로연구소
Identity V Gameplay - The Mobile Dead by Daylight
Download Links: http://bit.ly/2J692pS Identity V Facebook: https://www.facebook.com/IdentityV/ Message from Dead by Daylight Team: ...
TydeTyme
Dissonance - Disrupting Democracy: How Technology is Influencing Elections
U-M Dissonance Event Series panel discussion recorded Tuesday, November 1 in the Michigan League Ballroom. Both U.S. Presidential candidates shared ...
umichTECH
Corruption inside the UN: the Strategic Implications
Peter Gallo presented a lecture on corruption in the United Nations on May 23, 2018 at The Institute of World Politics. His talk included insight from his ...
The Institute of World Politics
K+S Legacy Project Potash Mine
Did you know that it's possible to mine potash with simply the dissolving power of hot water? The K+S Legacy Project is the first new mine in Saskatchewan in ...
Sask Wanderer
Twinkle Twinkle Little Star
Watch this video and MUCH more in the Super Simple App for iOS! ▻ http://apple.co/2nW5hPd Twinkle, twinkle, little star. How I wonder what you are.
Super Simple Songs - Kids Songs
DEFCON 16: Virtually Hacking
Speaker: John Fitzpatrick, Information Security Consultant - MWR InfoSecurity Own the VMware box and you get half the servers on the network for free.
Christiaan008
DEFCON 16: Owning the Users with The Middler
Speaker: Jay Beale, Senior Security Consultant and Co-Founder, Intelguardians Network Intelligence, Inc. This talk introduces a new open source, ...
Christiaan008
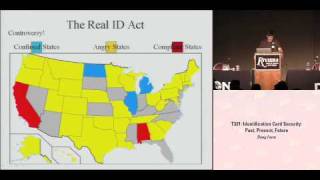
DEFCON 16: Identification Card Security: Past, Present, Future
Speaker: Doug Farre, Administrative Director, Locksport International Come learn how identification cards have taken over our lives, how they can be ...
Christiaan008
BlackHat 2016 - Cybersecurity Trends
Summary of BlackHat 2016 topics.
Smarttech247 - Managed Security Solutions
Cybersecurity and Health Care Information Technology
Presenter: Robin Saunders, River Valley Community College, Claremont, NH Cyber security isn't on the syllabus at any medical school, but maintaining effective ...
MPICTCenter
President Carter comments on Snowden
In an interview with Christiane Amanpour, Former U.S. President Jimmy Carter comments on the case of Edward Snowden. More from CNN at ...
CNN
DEFCON 16: The emergence (and use) of Open Source Warfare
Speaker: Peter Berghammer, CEO, Copernio Holding Company The presentation will deal briefly (20 minutes) with the concepts surrounding Open Source ...
Christiaan008
Insights into the Vulnerability of the Power System
Peter Pry, Executive Director of the EMP Task Force on National and Homeland Security, discusses the threat of an electromagnetic pulse (EMP) attack on our ...
The Mackenzie Institute
DEFCON 16: Beholder: New wifi monitor tool
Speakers: Nelson Murilo, Security Researcher Luiz 'effffn' Eduardo, Security Researcher Although it's not something new at all, network administrators are still ...
Christiaan008
Walter Mebane, "Using Agent-based Models to Simulate Electoral Equilibria, Including Frauds"
Walter Mebane (University of Michigan) presented a talk entitled "Using Agent-based Models to Simulate Electoral Equilibria, Including Frauds" to the ...
Methods Colloquium
What does the Main Grid Control Centre do?
In this video we get to explore the mission and operation of the Fingrid Main Grid Control Centre. The centralized control centre has three main tasks: ...
FingridOyj
Intel community trying to undermine Trump's presidency?
Former Rep. Dennis Kucinich (D-Ohio) on Gen. Michael Flynn resigning as President Trump's National Security Advisor and the divide between the intelligence ...
Fox Business
RESOLUTION(A FATHER-DAUGHTER RELATIONSHIP)
This short movie depicts the relationship of a woman with her father and her husband. Produced by Miracle Creations Director: P. S. Joardar D.O.P: Siddartha ...
Miracle Creations
DEFCON 16: Panel: Black vs. White: The complete life cycle of a real world breach
Panel: David Kennedy, Practice Lead: Profiling & e.Discovery, SecureState Ken Stasiak, President & CEO, SecureState Scott White, Senior Security Consultant, ...
Christiaan008
2018-10-24 CERIAS - 80/20 Rule-Cyber Hygiene
Recorded: 10/24/2018 CERIAS Security Seminar at Purdue University80/20 Rule-Cyber HygieneMark Loepker, SANMARKHygiene - it\'s good for your body ...
Purdue CERIAS
India rejects NSA leaker Edward Snowden's request for political asylum
SHOTLIST AP TELEVISION Bandar Seri Begawan, Brunei 1. Indian Foreign Minister Salman Khurshid walking towards media 2. SOUNDBITE (Korean) Salman ...
AP Archive
Facebook Hacker Cup 2011
credit: Facebook More Info: http://ow.ly/4ecbt.
AllInTech
DEFCON 16: Nail the Coffin Shut, NTLM is Dead
Speaker: Kurt Grutzmacher, Security Researcher Ever since SirDystic's SMBRelay release the weaknesses of the NTLM protocol have been repeatedly shown.
Christiaan008
MAKE your PAYLOAD seems LIKE an IMAGE | EXPLOIT | EASY SPREADING | WORKING 2020
malware #spreading #exploit Make your PAYLOAD seems like an IMAGE! Telegram: https://t.me/joinchat/AAAAAEdh-P-z06zwKuYucw DOWNLOAD: -ONLY ...
ItalianHackers
Identity — Town Square First Impressions Gameplay!
https://g2a.com/r/Psi (use code "PSI" for 3% cashback) DESCRIPTION Today we get our first taste of the first module for Identity, the Town Square module!
PsiSyn
CFD2019 Davos Cyber Adversaries and Public-Private Partnership
Adversarial actors in cyberspace – how can public – private – civil society engagement lead to eradication of cyber crime, criminalizing offenses and bring cyber ...
Cyber Future Foundation
Infrastructure Resilience
Follow along with the course eBook: https://systemsinnovation.io/books/ Take the full course: https://systemsinnovation.io/courses/ Twitter: http://bit.ly/2JuNmXX ...
Systems Innovation