How to Prepare Research Paper for Publication in MS Word (Easy)
... of the ACM,Computer,IEEE Transactions on Pattern Analysis and Machine Intelligence,IEEE Transactions on Computers,IEEE Transactions on Evolutionary ...
MJ Tube
IEEE 2016: DeyPoS: Deduplicatable Dynamic Proof of Storage for Multi-User Environments
We are ready to provide guidance to successfully complete your projects and also download the abstract, base paper from our website Note: Voice Video Listen ...
Java First IEEE Final Year Projects
IEEE Transactions on Intelligent Transportation Systems
Simulation results of a publication entitled Time-Optimal Maneuver Planning in Automatic Parallel Parking Using a Simultaneous Dynamic Optimization ...
柏李
Keynote - Frank Z Wang at SAI Conference 2014 - How will computers evolve over the next 10 years
Computer science has impact on many parts of our lives. Computer scientists craft the technologies that enable the digital devices we use every day and ...
SAIConference
Utilization Aware Power Management in Reliable and Aggressive Chip Multi Processors - March Chinese
With increasing transistor density on a single chip, processor design in the nanoscale era is hitting power and frequency walls. Due to these challenges, ...
ieeeComputerSociety
Analytical Fault Tolerance Assessment and Metrics for TSV-Based 3D Network-on-Chip-Chinese
Reliability is one of the most challenging problems in the context of three-dimensional network-on-chip (3D NoC) systems. Reliability analysis is prominent for ...
ieeeComputerSociety
Configurable XOR Hash Functions for Banked Scratchpad Memories in GPUs (0716 Chinese)
Scratchpad memories in GPU architectures are employed as software-controlled caches to increase the effective GPU memory bandwidth. Through the use of ...
ieeeComputerSociety
Enabling Energy-Efficient and Reliable Neural Network via Neuron-Level Voltage Scaling Chinese
With the platforms of running deep neural networks (DNNs) move from large-scale data centers to handheld devices, power emerge as one of the most ...
ieeeComputerSociety
High Performance Parallel Decimal Multipliers Using Hybrid BCD Codes 1217
A parallel decimal multiplier with improved performance is proposed in this paper by exploiting the properties of three different binary coded decimal (BCD) ...
ieeeComputerSociety
A Light-Weight White-Box Encryption Scheme for Securing Distributed Embedded Devices 1019
Distributed embedded devices are widely used in sensor networks and the Internet of Things for gathering and sending data. Many of them are deployed in an ...
ieeeComputerSociety
Graph Similarity and its Applications to Hardware Security
Hardware reverse engineering is a powerful and universal tool for both security engineers and adversaries. From a defensive perspective, it allows for detection ...
ieeeComputerSociety
Cloudlets Activation Scheme for Scalable Mobile Edge Computing with Transmission Power Control...
Mobile devices have several restrictions due to design choices that guarantee their mobility. A way of surpassing such limitations is to utilize cloud servers called ...
ieeeComputerSociety
Lec 23: How to Explore Computer Architecture?
Advanced Computer Architecture Course URL: https://swayam.gov.in/nd1_noc19_cs62/... Prof. John Jose Dept of Computer Science & Engineering IIT ...
NPTEL IIT Guwahati
Linear Branch Entropy: Characterizing and Optimizing Branch Behavior...0317 Spanish
In this paper, we propose linear branch entropy, a new metric for characterizing branch behavior. Linear branch entropy is independent of the configuration of a ...
ieeeComputerSociety
Latest Journal Impact Factor List 2020: Complete
Science journal complete list with latest impact factor.
Capsule
Adaptive Voltage Scaling in ZYNQ FPGAs
Check Nunez-Yanez J, "Adaptive Voltage Scaling with in-situ Detectors in Commercial FPGAs", IEEE transactions on Computers preprint, DOI ...
Jose Nunez-Yanez
HEAWS - Homomorphic Encryption on AWS F1
... and I. Verbauwhede IEEE Transactions on Computers, 2020. https://github.com/KULeuven-COSIC/HEAT ___ This video is prepared for participation in Xilinx ...
Furkan Turan
Opportunistic Mobile Networks- Part- III
Wireless Ad Hoc and Sensor Networks
[IEEE Transactions on Magnetics & InterMag 2014] A micro-robot - Jinsoo Kim
IEEE Transactions on Magnetics IEEE International Magnetics Conference (INTERMAG Europe 2014) Micro-robot Jinsoo Kim, Center for Bionics Korea Institute ...
Jinsoo Kim
Extending Unix Pipelines to DAGs (0917)
The Unix shell dgsh provides an expressive way to construct sophisticated and efficient non-linear pipelines. Such pipelines 4 can use standard Unix tools, ...
ieeeComputerSociety
A Compositional Approach for Verifying Protocols Running on On-Chip Networks (0718) Chinese
In modern many-core architectures, advanced on-chip networks provide the means of communication for the cores. This greatly complicates the design and ...
ieeeComputerSociety
A Light-Weight White-Box Encryption Scheme for Securing Distributed Embedded Devices (Chinese) 1019
Distributed embedded devices are widely used in sensor networks and the Internet of Things for gathering and sending data. Many of them are deployed in an ...
ieeeComputerSociety
Parallel Reproducible Summation
Reproducibility, i.e. getting bitwise identical floating point results from multiple runs of the same program, is a property that many users depend on either for ...
ieeeComputerSociety
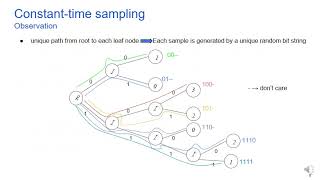
Constant-Time Discrete Gaussian Sampling (1118)
Sampling from a discrete Gaussian distribution is an indispensable part of lattice-based cryptography. Several recent works have shown that the timing leakage ...
ieeeComputerSociety
MPPA + Autoware on eMCOS: Localization of Self-driving software on Embedded Many Cores
Y.Maruyama, S.Kato, and T.Azumi, “Exploring Scalable Parallel Computing on NoC-based Embedded Many Cores," in IEEE Transactions on Computers ...
OsakaUniv EmbIV
CppCon 2016: Matt P. Dziubinski “Computer Architecture, C++, and High Performance"
Modern CPU architecture has continued to yield increases in performance through the advances in microarchitecture, such as pipelining, multiple issue ...
CppCon
Towards Optimal Multi-Level Checkpointing (0717)
We provide a framework to analyze multi-level checkpointing protocols, by formally defining a k-level checkpointing pattern.
ieeeComputerSociety
Secure Auditing and Deduplicating Data in Cloud
2015 IEEE Transaction on Cloud Computing For More Details::Contact::K.Manjunath - 09535866270 http://www.tmksinfotech.com and ...
manju nath
How to use the Encyclopaedia of Forms & Precedents
This is for students of Temasek Polytechnic who have access to the Library website http://spark.tp.edu.sg.
Benjamin Ang
Cloudlets Activation Scheme for Scalable Mobile Edge Computing with Transmission Power... Spanish
Mobile devices have several restrictions due to design choices that guarantee their mobility. A way of surpassing such limitations is to utilize cloud servers called ...
ieeeComputerSociety
Fast Coflow Scheduling via Traffic Compression and Stage Pipelining in Datacenter Networks Slide CN
Big data analytics in datacenters often involve scheduling of data-parallel jobs. Traditional scheduling techniques based on improving network resource ...
ieeeComputerSociety
IEEE Transactions on Signal Processing Top #5 Facts
Rishika Janaki
IEEE CIS "How to publish your research": Garrison Greenwood
... President for Publications, Former Editor-in-Chief (EiC) of IEEE Transactions on Evolutionary Computation http://www.youtube.com/watch?v=5fHMg0JkfqY 2.
CIS Cyprus
IEEE – TRANSACTIONS ON ANDROID
Final Year Students Project for IEEE Application Project||Embedded||Civil||Mechanical||Electronic Communication.
Raman Saravanan
An Error-Detection and Self-Repairing Method for Dynamically...(0617 Spanish)
Abstract—Reconfigurable systems are gaining an increasing interest in the domain of safety-critical applications, for example in the space and avionic domains.
ieeeComputerSociety
IEEE CIS "How to publish your research": Kay Chen Tan
... Former Editor-in-Chief (EiC) of IEEE Transactions on Evolutionary Computation http://www.youtube.com/watch?v=5fHMg0JkfqY 2. Prof. Kay Chen Tan, EiC of ...
CIS Cyprus
Analytical Processor Performance and Power Modeling Using Micro-Architecture...Spanish - 1216
Abstract—Optimizing processors for (a) specific application(s) can substantially improve energy-efficiency. With the end of Dennard scaling, and the ...
ieeeComputerSociety
A Novel Coding Scheme for Secure
E-SYSTEMS-TECHNO PVT LTD Website: www.esystems.co.in Email Id : info@esystems.co.in Phone: + 91 868 652 2186 + 91 868 652 2184 A-2, Ground Floor, ...
Ieee Projects
RTP general studies
RTP_Exam solving.
B100p Games
TEDxESADE - Jonathan Wareham - Creativity Lost? Computers and The Crisis in Creative Work
... Decision Support Systems, IEEE Transactions on Engineering Management, IEEE Computer, Journal of Medical Internet Research, Journal of the American ...
TEDx Talks
Lecture 27. Multiprocessors - Carnegie Mellon - Computer Architecture 2015 - Onur Mutlu
Lecture 27. Multiprocessors Lecturer: Prof. Onur Mutlu (http://users.ece.cmu.edu/~omutlu/) Date: Apr 6th, 2015 Lecture 27 slides (pdf): ...
Carnegie Mellon Computer Architecture
CERIAS Security: Automatic Debugging and Verification of RTL-Specified Real-Time Systems 4/6
Clip 4/6 Full title: Automatic Debugging and Verification of RTL-Specified Real-Time Systems via Incremental Satisfiability Counting and On-Time and Scalable ...
Christiaan008