Session on Cyber-Physical Systems Security
Follow us at : Facebook: https://www.facebook.com/ieeekerala Instagram: https://www.instagram.com/ieeekerala --- IEEE & IEEE ...
IEEE Kerala Section
Demo video for EchoFAS (IEEE TIFS 2022)
A short demo video for EchoFAS system. (Paper: Beyond the Pixel World: A Novel Acoustic-based Face Anti-Spoofing System for ...
Chenqi KONG
Bio-WISE - Biometric recognition with integrated pad: simulation environment
Bio-WISE (Biometric recognition with integrated pad: simulation environment) provides a simulator which allows investigating the ...
Pra Lab
Deep Neural Networks for Automated Object Detection within X-ray Baggage Security Imagery
An Evaluation Of Region Based Object Detection Strategies Within X-Ray Baggage Security Imagery (S. Akcay, T.P. Breckon), ...
Toby Breckon
Cryptophasia in Hardware: Physically Related Functions
Can two devices talk securely? We call this “Cryptophasia in Hardware” – a phenomenon that allows hardware circuits/devices ...
Secure Embedded Architecture Laboratory
IDENTITY-BASED ENCRYPTION TRANSFORMATION FOR FLEXIBLE SHARING OF ENCRYPTED DATA - IEEE PROJECT 2020
IDENTITY-BASED ENCRYPTION TRANSFORMATION FOR FLEXIBLE SHARING OF ENCRYPTED DATA - IEEE PROJECT 2020 ...
IEEE PROJECT VIDEOS 2020
Artificial Intelligence for Digital Forensics - Anderson Rocha @ University of Padova
Abstract: In this talk, we will discuss a panoramic view of digital forensics in the last 10 years and how it needed to evolve from ...
labDISP
Optical illusion protects PIN from shoulder-surfing attacks
Visit http://archive.nextanimationstudio.com or contact inquiries@nextanimation.com.tw to license this or any News Direct video ...
News Direct
Securing Your Fingerprints: Fuzzy Vault
Contents of video: 0:00 - Intro 0:11 - Problem Motivation 2:10 - Problem Statement 2:30 - Viewer Background 2:45 - Solution 8:05 ...
Mesons
IEEE 2017: Authorship Attribution for Social Media Forensics
We are ready to provide guidance to successfully complete your projects and also download the abstract, base paper from our ...
Java First IEEE Final Year Projects
Anomalieerkennung in Videodaten - Sichere Informationssysteme
Philipp Strasser und Samuel Sutter vom Masterstudiengang Sichere Informationssysteme haben sich im letzten Jahr in ihrem ...
FH OÖ Hagenberg
IEEE WIFS 2021 Keynote : Multimedia data recovery and its related workflows in digital forensics
Patrick De Smet (Belgian National Institute of Criminalistics and Criminology, Brussel, Belgium) This presentation provides an ...
Laura Bertojo
Digital Image Sharing by Diverse Image Media | IEEE | IEEE projects 2014
Conventional visual secret sharing (VSS) schemes hide secret images in shares that are either printed on transparencies or are ...
Renown Technologies
Talk on Security, Privacy and Trustworthiness in the AI World
This Talk is given by Dr. Karthik Nandakumar (Mohamed bin Zayed University of Artificial Intelligence)
IEEE SPS Gujarat Section
A High Performance Fingerprint Matching System for Large Databases | IEEE | IEEE projects 2014
Fingerprints are the biometric features most used for identification. They can be characterized through some particular elements ...
Renown Technologies
QoS-Aware User Association and Resource Allocation in LAA-LTE/WiFi Coexistence Systems 2019-20
QoS-Aware User Association and Resource Allocation in LAA-LTE/WiFi Coexistence Systems 2019-20 Download projects ...
MICANS INFOTECH PVT LTD
[TIFS 2019] Skeleton-based gait recognition demo (RFM)
RFM (Skeleton-based Gait Recognition via Robust Frame-level Matching) IEEE Transactions on Information Forensics and ...
Seokeon Choi
IEEE NETWORKING TOPICS - FINAL YEAR IEEE COMPUTER SCIENCE PROJECTS
TSYS Center for Research and Development (TCRD) is a premier center for academic and industrial research needs.
Tsys Globalsolutions
IEEE Computational Intelligence Society | Wikipedia audio article
This is an audio version of the Wikipedia Article: https://en.wikipedia.org/wiki/IEEE_Computational_Intelligence_Society 00:00:34 ...
wikipedia tts
Computation Resource Allocation and Task Assignment Optimization in Vehicular Fog Computing 2019-20
Computation Resource Allocation and Task Assignment Optimization in Vehicular Fog Computing: A Contract-Matching Approach ...
MICANS INFOTECH PVT LTD
Un computer può sapere chi sei da come scrivi? - Stilometria
Eccola! Finalmente un po' di paranoia, che non guasta mai, soprattutto con questo clima freddo. Ingredienti per 4 porzioni di ...
Output della mente
Three Minute Thesis (3MT) 2011 Winner - Matthew Thompson
Three Minute Thesis (3MT) Competition 2011 Winning presentation "Suspects, Science and CSI" by Matthew Thompson from the ...
The University of Western Australia
CCST | Everything You Need to Know About Cisco's New Certification
Cisco just announced a new entry level certification, the Cisco Certified Support Technician. But what does this mean for you? no ...
Brainmelt University
Message Passing Based Distributed Learning for Joint Resource Allocation - IEEE PROJECTS 2019-20
Message Passing Based Distributed Learning for Joint Resource Allocation in Millimeter Wave Heterogeneous Networks 2019-20 ...
MICANS INFOTECH PVT LTD
Document Clustering for Forensic Analysis An Approach-2013 PASS IEEE Projects
Ph: 0452 4243340; Mobile: 9840992340; http://pandianss.com Pandian Systems and Solutions Pvt Ltd 2nd Floor, No 393 ...
pass pandian
How to Trace Bitcoin Transactions (and avoid yours being traced)
In this video I show you a common way that bitcoin transactions can be traced, and some methods to avoid your transactions ...
Mental Outlaw
Smartphone privacy: IllusionPIN system protects your PIN from shoulder-surfing attackers - TomoNews
NEW YORK — A technology developed by researchers at New York University could defeat shoulder-surfing attackers by ...
TomoNews US
On General Trends in Security and Privacy - Bart Preneel
Bart Preneel received the Electrical Engineering degree and the Doctorate in Applied Sciences from the KU Leuven (Belgium).
METU Graduate School of Informatics
No Free Charge Theorem 2 0 How to Steal Private Information from a Mobile Device Using a Powerbank
Thanks to their omnipresence and multi-purposeness, users rely on smartphones to execute in few touches a wide range of ...
All Hacking Cons
JAVA PROJECT CODE IN TURKEY
Computer-aided design projects in java, Context-aware computing projects in java, Dependable and secure computing projects in ...
ieee papers
NextG Signal Processing Architectures: from mmWave to Deep Learning - Prof. Upamanyu Madhow
NextG Signal Processing Architectures: from mmWave to Deep Learning Professor Upamanyu Madhow ECE Department, UCSB ...
CSC CONICET
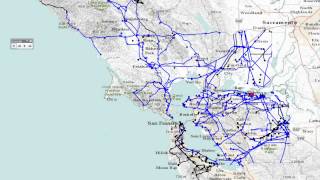
Demo of a potential cascading failure in San Francisco Bay area
This is a demo developed by the research team on Smart Grid Security at University of Rhode Island. It visualizes a simulated ...
Jun
IEEE 2017: Authorship Attribution for Social Media Forensics
We are ready to provide guidance to successfully complete your projects and also download the abstract, base paper from our ...
DHS Projects Bangalore
ieee journal explain in tamil|what is ieee |final year project ieee explain|ieee paper tamil explain
Journals Institute of Electrical and Electronics Engineers link: https://ieeexplore.ieee.org/browse/periodicals/title. IEEE Access ...
MAKE LABS INDIA
SYIRIS Demo
Video demonstration of SYIRIS, a MATLAB code package which can generate SYnthetic IRIS images. Jinyu Zuo; Natalia A.
Jinyu Zuo
A Unified Framework for Tracking Based Text Detection and Recognition from Web Videos
A Unified Framework for Tracking Based Text Detection and Recognition from Web Videos Download source code @ WWW.
MICANS INFOTECH PVT LTD
Open Commission Meeting - April 2010
April Open Commission Meeting, where the Commission discussed USF Reform NPRM and NOI, Mobile Roaming Order and ...
Federal Communications Commission
MSU Latent AFIS Overview
This is a video overview of the Michigan State University Latent Automatic Fingerprint Identification System. This software was ...
PRIP Lab, MSU
NetSpam A Network Based Spam Detection Framework for Reviews in Online Social Media
2017 IEEE Transaction on Information Forensics and Security For More Details::Contact::K.Manjunath - 09535866270 ...
manju nath
Key Updating for Leakage Resiliency With Application to AES Modes of Operation
2015 IEEE Transaction on Information Forensics and Security For More Details::Contact::K.Manjunath - 09535866270 ...
manju nath
Discovering Canonical Correlations between Topical and Topological Information in Document Networks
2018 IEEE Transaction on Knowledge and Data Engineering For More Details::Contact::K.Manjunath - 09535866270 ...
manju nath
IEEE 2016: An Exploration of Geographic Authentication Schemes
We are ready to provide guidance to successfully complete your projects and also download the abstract, base paper from our ...
Java First IEEE Final Year Projects